Defining the authorization scheme
Archived
9 Tasks
30 mins
Scenario
Front Stage's organizational structure for event planning is displayed as in the image given below.
The following requirements are provided with regards to security:
- Only sales executives and executive managers are allowed to see financial information.
- A sales executive is able to work on cases created by other sales executives. However, a sales executive is not able to access a peer’s case for an event larger than 10,000 attendees.
- Event managers are only able to work on cases assigned to them. However, the event manager's team lead can work on cases assigned to any event manager.
- Facility coordinators can only see and work on cases assigned to them.
- Executive officers can view cases throughout the life cycle and create new custom reports.
The following table provides the credentials you need to complete the exercise.
| Role | Operator ID | Password |
|---|---|---|
| Administrator | Admin@Booking | rules |
The following table provides a list of sample users that are available for testing.
| Department | Role | Operator ID | Password |
|---|---|---|---|
| Executives | Executive Officer and CEO | CEO@Booking | rules |
| Sales | Sales Executive | SalesExecutive1@Booking | rules |
| Sales | Sales Executive | SalesExecutive2@Booking | rules |
| Facility | Facility Coordinator specialized in Parking | FacilityCoordinator1@Booking | rules |
| Facility | Facility Coordinator specialized in Weather Preparation | FacilityCoordinator2@Booking | rules |
| Facility | Facility Coordinator specialized in Weather Preparation and Parking | FacilityCoordinator3@Booking | rules |
| EventManagers | Event Manager and Team Lead | EventManager1@Booking | rules |
| EventManagers | Event Manager | EventManager2@Booking | rules |
| EventManagers | Event Manager | EventManager3@Booking | rules |
Your assignment
Design and implement the authorization scheme to fulfill the requirements described earlier.
- Identify access groups and roles.
- Implement the above requirements.
Note: If the Admin@FSG operator record already exists:
Use “advanced/granular” mode when importing the RAP. You will be shown the Operator records included in the RAP. Permit the existing Admin@FSG and other Operator records to be updated.
Use “advanced/granular” mode when importing the RAP. You will be shown the Operator records included in the RAP. Permit the existing Admin@FSG and other Operator records to be updated.
Detailed Tasks
1 Solution detail
Create Units
Please add following Units:
| Organization unit |
|---|
| Executives |
| EventManagers |
| Facilities |
| Sales |
Create Operators and Assign Skills
Create/Update Skills
Please add CEO , TeamLead, Parking , Weather Skills with Low-High range 1-10.
Create below Operators with Manager access group and default access group.
| SalesExecutive1@Booking |
| SalesExecutive2@Booking |
For each of the following operators, update skills and ratings for the operators defined in the table.
| Operator ID | Skill(s) and rating |
|---|---|
| CEO@Booking | CEO (5), TeamLead (5) |
| FacilityCoordinator1@Booking | Parking (5) |
| FacilityCoordinator2@Booking | Weather (5) |
| FacilityCoordinator3@Booking | Parking (5), Weather (5) |
| EventManager1@Booking | TeamLead (5) |
Access groups and roles
System generated roles
The New Application wizard creates a Booking:Administrator / Booking:Authors role and two user roles: Booking:User and Booking:Manager.
Users with the Booking:User role can open any case in the application and perform any assignment. The Booking:Manager role provides the ability to create and update reports, delegated rules, and work groups.
Check the Booking access groups
Create and configure access groups and roles for each department since access is granted based on the department.
When the Event Booking application was first developed the following access groups may have created. If so, the access group names may not comply with our naming conventions, so you will rename them as needed as listed in the following table.
| POC access group name | New access group name |
|---|---|
| Booking:FacilityCoordinator | Booking:Facilities |
To rename the existing access groups, do the following:
- From your exercise system, log on as Admin@Booking.
- From the DEV Studio menu, go to System > Configure > Refactor > Rules and open the Search/Replace a String wizard.
- Select Search/Replace a String.
- In the Original String Value field, enter Booking:FacilityCoordinator. In the New String Value field enter Booking:Facilities.
- Set Limit search to RuleSets in my RuleSet list? to No.
- In the Select RuleSet Scope section, select the Booking ruleset. Only select the Booking ruleset. We can do this because all the affected rules we need to refactor are in the Booking ruleset.
- Select Next. This page displays a report showing the number of Records with Occurrences and Occurrences Found.
- Select Next. This page displays a report showing the Selectable rules available which have references to the class being refactored. Enable the check box next to Rule Type in the header of the report. This selects all the records. Optionally, you can Export to Excel to keep a log of the affected records.
- Select Finish. This page displays a confirmation that the refactoring process is complete and displays a report of the rule and data instances that were not refactored. Optionally, you can Export Page to Excel and/or Review Log.
- Select Done.
- Please Save as the Booking:Facilities Access group to create three more access groups as belows :
Access Group Booking:Executives Booking:Sales Booking:EventManagers
Create Event Booking roles
Create the following roles for each department since permissions and privileges are granted based on the department. Save the roles to the Event ruleset.
| Role name identifier | Label | Dependent on |
|---|---|---|
| Booking:Executive | Executive | PegaRULES:WorkMgr4 |
| Booking:SalesExecutive | Sales Executive | PegaRULES:WorkMgr4 |
| Booking:EventManager | Event Manager | PegaRULES:WorkMgr4 |
| Booking:FacilityCoordinator | Facility Coordinator | PegaRULES:WorkMgr4 |
Assign roles to the Event Booking access groups
To the renamed access groups, assign the following roles. Remove all other roles.
| Access group | Roles |
|---|---|
| Booking:Executives | Booking:Executive, Booking:Manager, Booking:User, PegaRULES:PegaAPI |
| Booking:Sales | Booking:SalesExecutive, Booking:User, PegaRULES:PegaAPI |
| Booking:Facilities | Booking:FacilityCoordinator, Booking:User, PegaRULES:PegaAPI |
| Booking:EventManagers | Booking:EventManager, Booking:User, PegaRULES:PegaAPI |
Create Event Booking work groups
Create the following work groups for each department because work is often assigned to them. Save the work groups to the Event ruleset. Also add the authorized managers named Admin@Booking and Author@Booking to each work group.
| Work group identifier | Description | Manager | Default workbasket |
|---|---|---|---|
| Executives@FSG | FSG Executives | CEO@Booking | Booking:Executives |
| Sales@FSG | FSG Sales | SalesExecutive1@Booking | Booking:Sales |
| EventManagers@FSG | FSG Event Managers | EventManager1@Booking | Booking:EventManagers |
| Facilities@FSG | FSG Facility Coordinators | FacilityCoordinator1@Booking | Booking:Facilities |
Create/Update Event Booking workbaskets
Create/Update the following workbaskets.
| Workbasket | Organization unit | Work group | Role |
|---|---|---|---|
| Booking:Executives | Executives | Executives@FSG | Booking:Executive |
| Booking:EventManagers | EventManagers | EventManagers@FSG | Booking:EventManager |
| Booking:Facilities | Facilities | Facilities@FSG | Booking:FacilityCoordinator |
| Booking:Sales | Sales | Sales@FSG | Booking:SalesExecutive |
Update to the operators
For each of the following operators, update the default Access Group, Work groups & Unit.
| Operator ID | Default Work group | Default Access Group | Unit |
|---|---|---|---|
| CEO@Booking | Executives@FSG | Booking:Executives | Executives |
| SalesExecutive1@Booking | Sales@FSG | Booking:Sales | Sales |
| SalesExecutive2@Booking | Sales@FSG | Booking:Sales | Sales |
| FacilityCoordinator1@Booking | Facilities@FSG | Booking:Facilities | Facilities |
| FacilityCoordinator2@Booking | Facilities@FSG | Booking:Facilities | Facilities |
| FacilityCoordinator3@Booking | Facilities@FSG | Booking:Facilities | Facilities |
| EventManager1@Booking | EventManagers@FSG | Booking:EventManagers | EventManagers |
| EventManager2@Booking | EventManagers@FSG | Booking:EventManagers | EventManagers |
| EventManager3@Booking | EventManagers@FSG | Booking:EventManagers | EventManagers |
2 Allow Executive Officers access to cases throughout the Event Booking life cycle
To allow Executive officers to view cases throughout the life cycle, edit their operator IDs and Do the following:
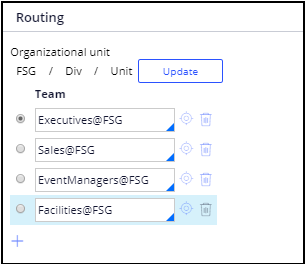
- Open the following operator ID records: CEO@Booking. In the Routing section of the Work tab, do the following:
- Add the following work groups: Executives@FSG, Sales@FSG, EventManagers@FSG, and Facilities@FSG.
- Specify Executives@FSG as the default.The completed section looks like the following image.
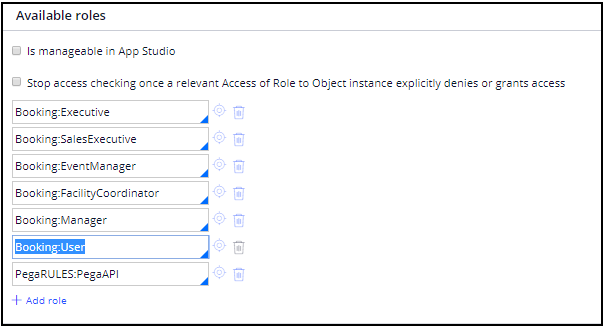
- Open the Booking:Executives access group.
-
In the Definition tab, add the following available roles: Booking:Executive, Booking:SalesExecutive, Booking:EventManager, Booking:FacilityCoordinator, Booking:Manager, Booking:User and PegaRULES:PegaAPI.
The completed access group looks like the following image.
-
Save the Executive access group.
Update Event Booking case type routing
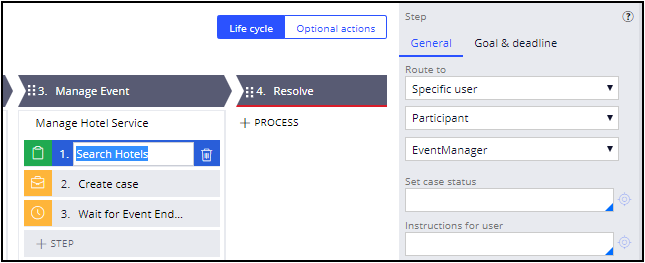
- From the Cases Explorer, open the Event Booking case type.
- in the Preparations stage, open the Hotels process. Open the Select Search Hotels assignment properties panel and verify that Specific user is set to .EventManager as shown in the following image.
Update Parking case type routing
- From the Cases Explorer, open the Parking case type.
- In the Preparation stage, open the Prepare for Parking process. Open the Reserve Shuttles assignment properties panel and verify the following settings.
Field Setting Route to Custom Assignment type Worklist Router ToLeveledGroup Workgroup Facilities@FSG Skill Parking - In the Execution stage, open the Collect Results process. Open the Enter Number of Cars Parked assignment properties panel and check verify the following settings.
Field Setting Route to Custom Assignment type Worklist Router ToWorkParty Party FacilityCoordinator - In the Preparation stage, open the Prepare for Parking process. On the Reserve Shuttles connector, open the ReserveShuttles flow action. On the flow action Action tab, in the Post-processing section, enter the following settings.
Field Setting Run activity addWorkObjectParty PartyRole parameter Facility coordinator PartyClass parameter Data-Party-Operator PartyModel parameter CurrentOperator The completed Run activity settings are shown in the following image.
Update Weather case type routing
-
In the Forecast Weather process of the Forecasting stage, open the Track Preparation assignment properties panel and verify that it is configured as followed.
Field Setting Route to Custom Assignment type Worklist Router ToLeveledGroup Workgroup Facilities@FSG Skill Weather -
In the Prepare for Weather process of the Preparing stage, open the Review Preparations assignment properties panel and verify that it is configured as follows.
Field Setting Custom Custom Assignment type Worklist Router ToWorkParty Party FacilityCoordinator
3 Enable attribute based access control (ABAC) security
You will use ABAC to configure your authorization scheme. Starting from pega 8.2, ABAC is enabled by default.
Restrict access to financial information using ABAC
To restrict access to the financial information as described in the scenario, you will:
- Create SalesExecutive and ExecutiveOfficer access when records to test if an operator belongs to the sales executives or executive officers access group.
- Create a SalesAndExecutives access control policy condition that references your new access when records.
- Create a RestrictFinancialInformation read properties access control policy that references your new access control policy condition. Users defined in the SalesAndExecutives access control policy condition can view the .Profit , .Totalcost, .TotalPrice, .DiscountPercentage, .PricingDisplay.EventPrice, .PricingDisplay.HotelServicePrice properties.
Create Sales Executive and ExecutiveOfficer access when records
- In the Records Explorer, expand the Security category.
- Select Access When record type.
- Click Create.
- In the new record form, enter the following.
Field Setting Label Sales Executive Apply to FSG-Booking-Work-BookEvent Add to ruleset Event - Click Create and open to create the new access when record.
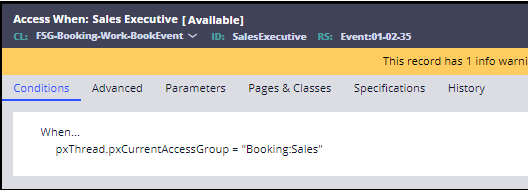
- On the Conditions tab, enter the following When... expression
pxThread.pxCurrentAccessGroup = "Booking:Sales".
The completed Conditions tab looks like the following image.
- Save the new SalesExecutive access when record.
- Repeat steps 1.a. through 1.c.
- In the new record form, enter the following.
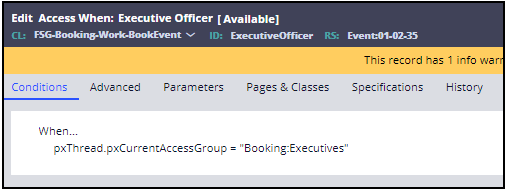
Field Setting Label Executive Officer Apply to FSG-Booking-Work-BookEvent Add to ruleset Event - Click Create and open to create the new access when record.
- On the Conditions tab, enter the following When... expression:
pxThread.pxCurrentAccessGroup = "Booking:Executives"
The completed Conditions tab looks like the following image.
- Save the new ExecutiveOfficer access when record.
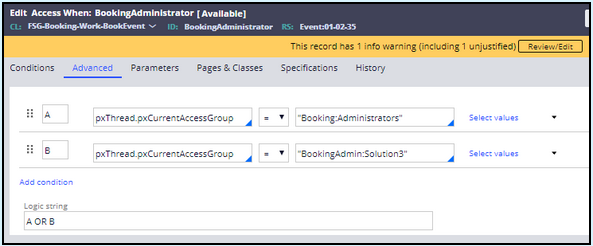
Note: You should also create an BookingAdministrator access when record with pxThread.pxCurrentAccessGroup = "Booking:Administrators" or "BookingAdmin:Solution3" expression so you can continue editing and viewing the restricted properties as Admin@Booking.
Create an SalesAndExecutives access control policy condition
- Open the Records Explorer.
- Expand the Security category.
- Select Access Control Policy Condition record types.
- Click Create.
-
In the new record form, enter the following :
Field Setting Label Sales And Executives Apply to FSG-Booking-Work-BookEvent Add to ruleset Event - Click Create and open to create the new SalesAndExecutives access control policy condition.
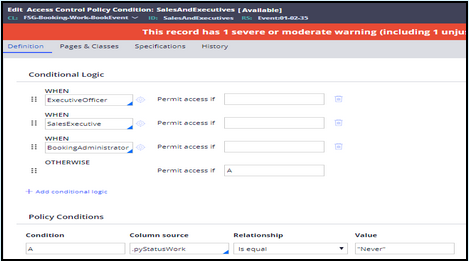
- In the access control policy condition Definition tab, in the Conditional Logic section, add the ExecutiveOfficer and SalesExecutive access when records you created.
-
Although not required, in the Policy Conditions section, specify a condition that always returns false to ensure that access is only provided if one of the access when rules evaluates to true.
- Save the new SalesAndExecutives access control policy condition record.
Note: You should also add a BookingAdministrator access when condition so you can continue editing and viewing the restricted properties as Admin@Booking.
The completed Definition tab looks like the following image.
The completed Definition tab looks like the following image.
Create a RestrictFinancialInformation access control policy
- Open the Records Explorer.
- Expand the Security category.
- Select Access Control Policy record types.
- Click Create.
-
In the new record form, enter the following.
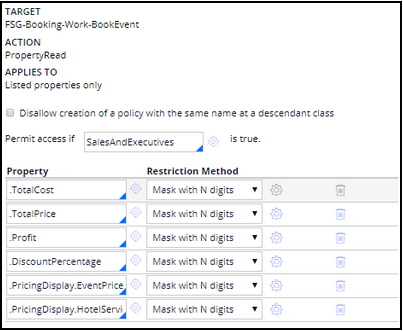
Field Setting Label Restrict Financial Information Action PropertyRead Apply to FSG-Booking-Work-BookEvent Add to ruleset Booking - Click Create and open to create the new RestrictFinancialInformation access control policy.
- In the access control policy Definition tab, in the Permit access if field, enter the SalesAndExecutives policy control policy condition you created.
- Add the.Profit , .Totalcost, .TotalPrice, .DiscountPercentage, .PricingDisplay.EventPrice, .PricingDisplay.HotelServicePrice properties. For all of the properties, use Mask with N digits as the Restriction Method.
The completed Definition tab looks like the following image.
- Save the new RestrictFinancialInformation access control policy record.
4 Restrict access to Event Booking cases using ABAC
To restrict access to the Event Booking cases as described in the scenario you will:
- Create the EventManager access when record to test whether an operator is in the event manager access group.
- Create the TeamLeadEventManager access when record to test whether an operator is in the Event Manager access group and has a Team Lead skill.
- Configure the properties used in the access control policy condition so that the properties can be used in search and in reports.
- Create a HasEventReadAccess access control policy condition that references your new access when conditions and includes policy conditions and access permissions.
- Create a RestrictEventAccess access control policy that references your new access control policy condition.
Create EventManager and TeamLeadEventManager access when records
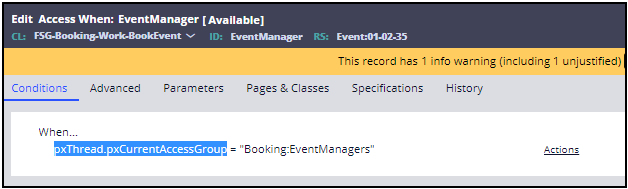
- Create the EventManager access when record to test whether an operator belongs to the EventManagers access group. Do the following:
- From the Records Explorer, expand the Security category.
- Select Access When record types.
- Click Create.
- In the new rule form, enter the following settings.
Field Setting Label Event Manager Apply to FSG-Booking-Work-BookEvent Add to ruleset Event - Click Create and open to create the EventManager access when record.
-
In the Conditions tab, enter the following When... expression:
pxThread.pxCurrentAccessGroup = "Booking:EventManagers".
The completed Conditions tab looks like the following image. - Save the new EventManager access when record.
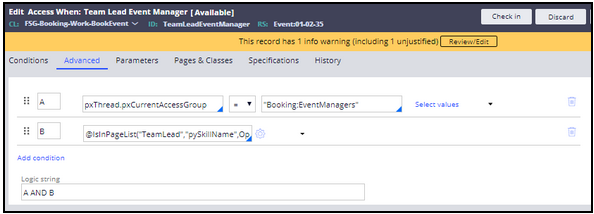
- Create the TeamLeadEventManager access when record to test whether an operator belongs to the Event Managers access group and has the TeamLead skill. Do the following:
- Repeat steps 1.a. through 1.c.
- In the new rule form, enter the following settings.
Field Setting Label Team Lead Event Manager Apply to FSG-Booking-Work-BookEvent Add to ruleset Event - Click Create and open to create the TeamleadEventManager access when record.
-
In the Conditions tab, use the following When... expression:
pxThread.pxCurrentAccessGroup = "Booking:EventManagers" AND function @IsInPageList("TeamLead","pySkillName",OperatorID.pySkills) .The completed Conditions tab looks like the following image.
- Save the new TeamLeadEventManager access when record.
Configure the access control policy condition properties
Before you can configure the new HasEventReadAccess access control policy condition, you must do the following;
- Create a new Property EventManager and populate
- Optimize the .EventManager and .NumAttendees properties for reporting.
- Make NumAttendees a filterable search property.
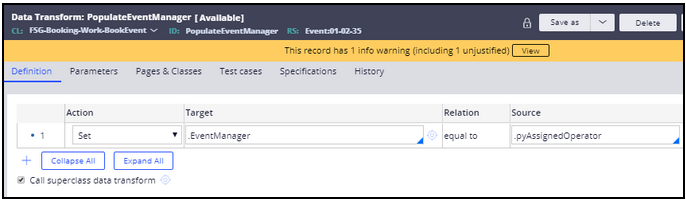
Create a new Property EventManager and populate
- Create a new text type property EventManager in class FSG-Booking-Work-BookEvent.
- Create a new Data transform PopulateEventManager to populate EventManager from .pyAssignedOperator as below:
- Update the flow action ManagerAssignment - Add the Data transform PopulateEventManager on the Post processing as below:
Optimize the EventManager and NumberOfAttendee properties
In the App Explorer, right-click the following properties and select Optimize for reporting.
- (FSG-Booking-Work-BookEvent) EventManager
- (FSG-Booking-Work-BookEvent) NumberOfAttendees
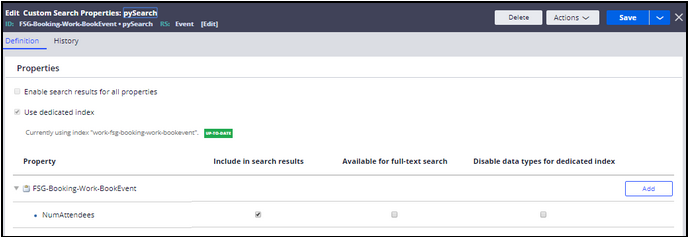
Make NumAttendees a filterable search property
- In the DEV Studio header, select Create > SysAdmin > Custom Search Properties.
- Enter FSG-Booking-Work-BookEvent in the Class Name field and then click Create and open.
- In the record header, set the Associated RuleSet to Event.
- Enable "Use dedicated index" and Create dedicated index.
- In the custom search properties Definition tab, select the FSG-Booking-Work-BookEvent property and then click the add button to open the Property Configurations dialog.
- In the Property Configurations dialog, select the NumAttendees property and then click Submit to save your updates and close the dialog.
-
Expand FSG-Booking-Work-BookEvent and select the Include in search results check box.
The completed Definition tab on the custom search properties record looks like the following image.
- Save the FSG-Booking-Work-BookEvent • pySearch custom search properties record.
5 Configure the HasEventReadAccess access control policy condition
- In the Records Explorer, expand the Security category.
- Select Access Control Policy Condition record types.
- Click Create.
- In the new rule form, enter the following.
Field Setting Label Has Event Read Access Apply to FSG-Booking-Work-BookEvent Add to ruleset Event - Click Create and open to create the HasEventReadAccess access control policy condition.
- On the Pages & Classes tab, add Page name OperatorID using Class Data-Admin-Operator-ID.
- On the Definition tab, do the following:
- in the Conditional Logic section, add the TeamLeadEventManager, EventManager, and SalesExecutive access when records you created as conditions.
-
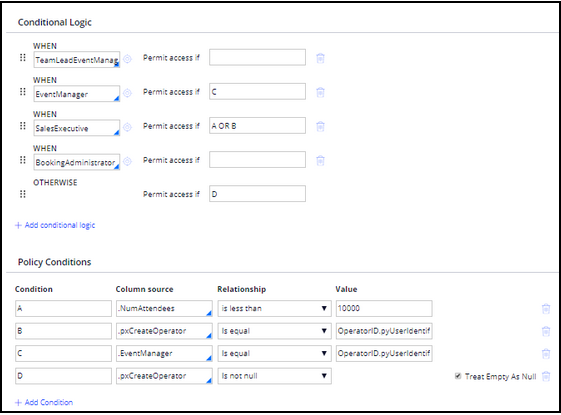
In the Policy Conditions section, specify the following conditions. Condition D always returns true to ensure that access is not prevented if none of the access when rules evaluates to true.
Condition Column source Relationship Value A .NumberOfAttendees is less than 10000 B .pxCreateOperator Is equal OperatorID.pyUserIdentifier C .EventManager Is equal OperatorID.pyUserIdentifier D .pxCreateOperator Is not null The completed Definition tab on the access control policy condition record looks like the following image.
- Save the HasEventReadAccess access control policy condition.
Create the RestrictEventAccess access control policy
In the Event Booking case type, create an access control policy for Read to restrict access to the Event Booking cases.
- Open the Records Explorer.
- Expand the Security category.
- Select Access Control Policy record types.
- Click Create.
- In the new rule form, enter the following settings.
Field Setting Label Restrict Event Access Apply to FSG-Booking-Work-BookEvent Add to ruleset Event Action Read - Click Create and open to open the new RestrictEventAccess access control policy.
-
In the Permit access if field, enter the HasEventReadAccess access control policy condition you created.
The completed Read • RestrictEventAccess access control policy is shown in the following image.
- Save the RestrictEventAccess access control policy.
Restrict access to facility cases
You can restrict opening Facility cases using role based access control. To do so, open the Facility case type and use the Access Manager to configure No Access for Perform.
6 Validate your work
- Log off as Admin@Booking.
- Log on as Author@Booking, and create a new Event Booking Case. Notice the .Profit , .Totalcost, .TotalPrice, .DiscountPercentage fields are all masked and are read-only. Log off.
-
Log on as SalesExecutive1@Booking, and create a new Event Booking Case. Notice the .Profit , .Totalcost, .TotalPrice, .DiscountPercentage, .PricingDisplay.EventPrice, .PricingDisplay.HotelServicePrice fields are not masked and are editable.
- Create two Event Booking cases one with under 10,000 attendees and another with more then 10,000 attendees. Do not complete the Customer Approval step in either case. Log off.
- Log on as SalesExecutive2@Booking, and switch to the Case Manager portal and do the following:
- On the Dashboard select Sales Executive 1 in the Team members section to view SalesExecutive1@Booking's open cases.
- Select Customer Approval for the case with under 10,000 attendees. As a result, you should be able to work on the case.
- Select Customer Approval for the case with more than 10,000 attendees. As a result, you should receive an error message to the effect that, "Access Control Policy denied access for class FSG-Booking-Work-BookEvent and action Open."
- Log out.
- Log on as EventManager2@Booking. Switch to the Case Manager portal and do the following:
- On the Dashboard select Event Manager 1 in the Team members section to view EventManager1@Booking's open cases.
- Select Approve Assignment for any case listed. As a result, you should receive an error message to the effect that, "Access Control Policy denied access for class FSG-Booking-Work-BookEvent and action Open."
- Log out.
- Log on as EventManager1@Booking. Switch to the Case Manager portal and do the following.
- On the Dashboard select Event Manager 2 in the Team members section to view EventManager2@Booking's open cases.
- Select Approve Assignment for any case listed. As a result, you should be able to work on the selected case.
7 Alternative approaches
The following alternative approaches are presented. They do not have to be developed. The detailed instructions provided are a guide in case you would like to experiment using role-based access control (RBAC) to restrict access to Event Booking cases or restrict access to Facilities assignments using ABAC.
Restrict access to financial information
There are no alternative approaches for restricting access to the financial information.
Restrict access to events cases using RBAC
Create a role for events and add it to appropriate access groups. Use the Access Manager to create an Access of Role to Object record with an access when record defining the restrictions.
Restrict access to Event Booking cases: Comparing RBAC and ABAC
The following table describes the pros and cons of each approach.
| Design | Pros | Cons |
|---|---|---|
| Attribute based access control | Easy to configure | Not shown in Access Manager |
| Role based access control | Shown in Access Manager | Requires an additional role |
Restrict access to Facilities assignments using ABAC (optional)
- For the Assign-Worklist class, create an access when condition named FacilityCoordinator in the Event ruleset.
-
In the Conditions tab, use the following When... expression:
pxThread.pxCurrentAccessGroup = "Booking:Facilities"
The Conditions tab should look like the following image.
- For the Assign-Worklist class, create a new FacilityCaseAssignedToMe access control policy condition in the Event ruleset.
- In the Pages & Classes tab on the access control policy condition record, enter OperatorID in the Page name field and enter Data-Admin-Operator-ID in the Class field.
-
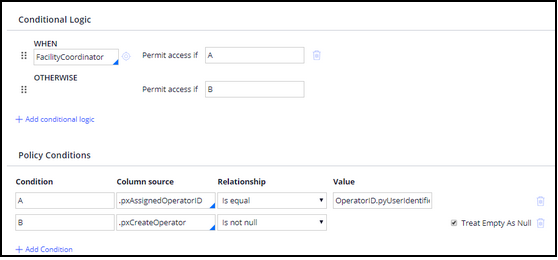
In the Definition tab, check if the user is a facility coordinator, and check if the case is assigned to that user. For all others, grant access.
The Definition tab configuration is shown in the following image. - For the Assign-Worklist class, create a RestrictFacilityCases access control policy in the EventBooking ruleset. Set the Action to Read to restrict other facility coordinators from opening the assignment and performing work.
-
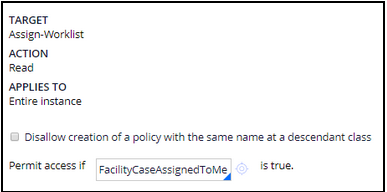
In the Permit access if field, enter the FacilityCaseAssignedToMe access control policy condition you created.
The access control policy should look like the following image.
Restrict access to Facilities assignments: comparing RBAC and ABAC
The following table describes the pros and cons of each approach.
| Design | Pros | Cons |
|---|---|---|
| Attribute based access control | Easy to configure | Not shown in Access Manager |
| Role based access control | Shown in Access Manager | Requires an additional role |
8 Solution RAP file
You can import the solution RAP file for this exercise to view the completed solution. The Read • RestrictFacilityCases access control policy, described in the lesson as optional, is implemented in the solution. The record availability is set to Blocked so you can experiment with the record.
The solution file does not contain a complete implementation of all the authorization requirements specified in the Front Stage Scenario Requirements. As a challenge exercise, you can implement all the requirements using a combination of RBAC and ABAC.
9 Solution download
Authorization_Scheme_Solutions.zip
(145.5 KB)