Log files
Pega Platform™ writes errors, warnings, and other information to a collection of log files to help you debug and maintain the health of your application. System architects review log files to investigate application issues during development, improving application quality. System administrators monitor log files to identify potential application or system issues in production.
Log files for application issues
Log files capture event notifications ranging from routine system status information to severe errors that can cause an application to quit unexpectedly. An appender manages each log and determines the type of events written to the log file. The available log files vary depending on the log file appenders that are configured in the system settings.
Pega Platform uses the following common log files:
- The PEGA log contains warnings, errors, and information about internal operations. This log is also known as the console log or system log, and you can use it for debugging the application.
- The ALERT log contains performance-related alerts triggered when an operation exceeds the specified performance threshold.
- The ALERTSECURITY log contains alerts (identified by the prefix SECU) that suggest improper configuration of Internet Application Composer facilities or overt attempts to bypass system security features on the Pega Platform node through URL tampering.
- The BIX log contains entries generated by the Business Intelligence Exchange (BIX) during extract operations. BIX is an optional add-on product that extracts transactional data from the Pega database into formats suitable for exporting to a reporting data warehouse, operational data store (ODS), or other downstream processes.
- The CLUSTER log contains information about the setup and run-time behavior of the cluster.
- The log contains information about the data flow events in the system, such as the number of running threads and newly created or stopped threads.
- The MOBILE log contains information about the running of a mobile application. You can retrieve logs for a user and specify how much information you want to include in the file.
- The PegaRULES-SecurityEvent log contains information about security-related events such as login failures or password changes.
Note: Pega Platform manages logs based on which appenders are configured. For example, to log performance data for services, you add SERVICES-PAL in the prlog4j2.xml configuration file for the node. For more information about performance statistics for services, see Viewing performance statistics for services.
Log files in Pega Cloud® environments
The following log files are available in Pega Cloud® environments:
- The log contains debugging information about system errors, exceptions, debug statements, and messages not specified as alerts.
- The log contains the setup and run-time behavior information of the underlying infrastructure on which a Pega environment runs.
- The log contains diagnostic messages for failures and system events that exceed performance thresholds.
- The log contains alerts generated when the security of a Pega web node is at risk.
- The log contains security events generated by a Pega web node.
- The log contains events that affect data flow runs and queue processors, which internally initiate data flow runs.
- The log contains performance details for each requestor that Pega Platform generates once an hour and at logoff.
- The log contains a record of each request to your application that includes different parameters in the HTTP request.
Note: For more information about Pega log types available in Pega Cloud environments, see Understanding and obtaining Pega log files.
Log utilities
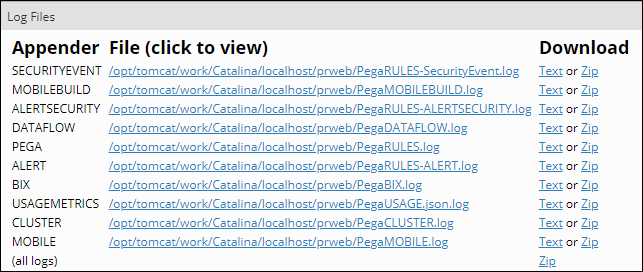
You access log files from the Log utilities section of the Logs tab in Dev Studio (Configure > System > Operations > Logs) to open the Log utilities. The Log utilities section includes a list of log file appenders and an external log viewer. Clicking Log files displays a list of the log file appenders that are active on the system.
The following figure shows an example of each appender with a link to view or download the log file as an unformatted text file or as a compressed ZIP file:
Note: Downloading a log file requires administrator credentials for the application server that hosts Pega Platform. You can also view log files using an external log viewer, such as Kibana. To learn more about viewing log files in an external viewer, see Viewing log files in an external log viewer.
For Pega Cloud systems, you can download specified log files using the My Cloud portal or work with Pega Cloud so you can stream log files to a preferred repository. For more information about downloading log files, see Downloading log files
For Pega Cloud systems, you can download specified log files using the My Cloud portal or work with Pega Cloud so you can stream log files to a preferred repository. For more information about downloading log files, see Downloading log files
In the following image, click the + icons to learn more about viewing the PEGA log file contents:
PegaRULES Log Analyzer
The PegaRULES Log Analyzer (PLA) is a standalone web application that developers and system administrators can use to view consolidated summaries of system log data.
Use the PLA to test new or reconfigured Pega Platform applications during user acceptance testing (UAT), performance and stress testing, and immediately after deployment into a production environment. Testing reconfigured applications during UAT, during performance testing, and right after deployment is important because performance, stability, and scaling issues are most likely to occur during these times.
The PLA consolidates and summarizes the ALERT, PEGA, and Garbage Collection (GC) logs. The log data provides key information about operational and system health that developers and system administrators can use to quickly identify, diagnose, and address performance issues.
Tip: The PLA is available from the Marketplace on Pega Community. To learn more about the PLA, see the Pega Marketplace overview PegaRULES Log Analyzer.
Override log level settings
A system administrator can override log level settings in Admin Studio to control which logging events are displayed in the PEGA log by creating a log category.
In earlier versions of Pega Platform without log categories, customization of logs occurred by updating the prlogging.xml or prlog4j2.xml files. For each system event, the prlog4j2.xml configuration file defines the threshold for determining which events to record in the logs. Events are recorded only for the selected logging level and higher. For example, if an event is configured with the ERROR logging level, only FATAL or ERROR events are noted in the log, while the system ignores INFO events. In a multi-node Pega environment, you can create separate prlog4j2.xml files for each node.
Note: If you update your application to Pega Platform version 8.7 or later, it is advisable to move log level customizations to Log Category I. To learn more about structuring log messages into categories, see Creating log categories for debugging. In addition, rulesets and the class hierarchy are irrelevant to logging. For example, if an appender includes logging events for an activity named Data-Party.Research and your system include several activities of that name; executions on the current node of any of these activities can produce logged events.
Tip: When debugging an activity, you can use the Log-Message method with the logging level set to InfoForced to add an event to the PEGA log regardless of settings in the prlog4j2.xml file or the Log Category. To reduce log entries and improve performance in production systems, remove InfoForced steps or convert them to comments when you finish debugging the activity.
Check your knowledge with the following interaction:
This Topic is available in the following Module:
If you are having problems with your training, please review the Pega Academy Support FAQs.
Want to help us improve this content?
