Authentication design considerations
Authentication design considerations
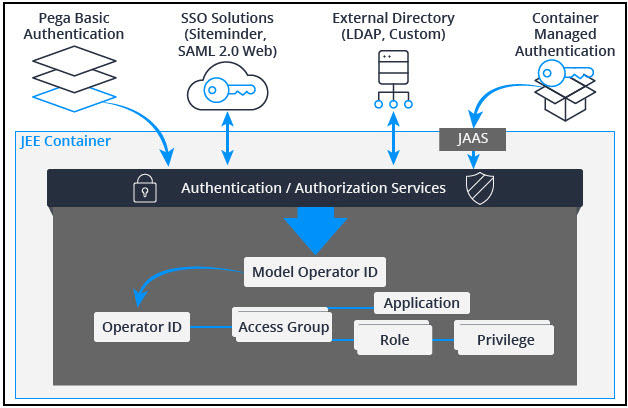
Authentication is proving to the application you are who you say you are. Each organization has policies on how users are authenticated into the application. Most organizations use some form of single sign on. If the organization is running an enterprise tier deployment, it may be using container-based authentication or JAAS or JEE security. If so, this affects how you design your authentication scheme and your application.
In short, the Pega application implements to the organization's authentication policy. For more information on authentication protocols supported by Pega, see the Pega Community article: Authentication in the Pega Platform and the Pega Help Topic: Authentication services .
Pega 8 has replaced PRBasic with Basic credentials and also added support for Anonymous, Oauth2, OIDC (Open ID Connect), and Kerberos.
Pega can be the Identity Provider (IdP) or the IdP can be external. An example of an external Identity Provider is Microsoft’s Active Directory Federated Service (ADFS), which is used on-premise as well as within Microsoft’s Azure cloud offering.
Pega is the IdP when the AuthenticationType used to access Pega is Basic credentials. Someone accessing Pega this way would not have “Use external authentication” checked within the Security tab on their Operator record.
If you are having problems with your training, please review the Pega Academy Support FAQs.
Want to help us improve this content?
