Authentication design considerations
Authentication in Pega Platform™ ensures that only users and systems with verified identities can access your applications. Each organization has policies on how user authentication occurs in the application. Most organizations use single sign-on (SSO). If the organization runs an enterprise-tier deployment, it might use container-based authentication or JAAS or JEE security. The container-based setup impacts how you design your authentication scheme and your application.
The Pega Platform application implements the authentication policy of the organization. For more information about the authentication protocols that Pega Platform supports, see Authentication.
The following diagram shows the different protocols for user logins that Pega Platform supports and how the system maps the operator ID with an access group, roles, and privileges to access the application securely. Pega Platform uses basic credentials and supports SAML 2.0, Anonymous, Oauth2, OIDC (Open ID Connect), token credentials, custom, and Kerberos.
Pega Platform can act as the identity provider (IdP), or it can use an IdP to authenticate users. For example, Active Directory Federation Services (ADFS) by Microsoft is an external IdP, which is used on-premise version of Pega Platform and in the Microsoft Azure cloud offering.
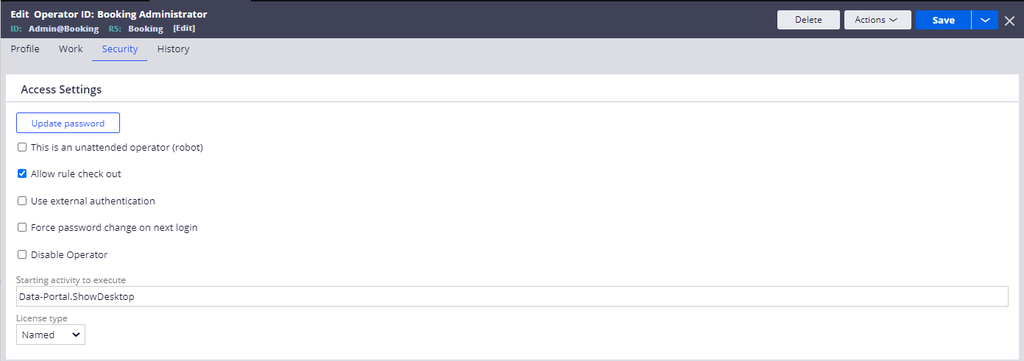
Pega Platform is the IdP when the setting of authentication type is Basic credentials. You configure basic credentials to authenticate users on the Security tab of the Operator ID record of a user by clearing the Use external authentication checkbox, as shown in the following figure:
Check your knowledge with the following interaction:
This Topic is available in the following Module:
If you are having problems with your training, please review the Pega Academy Support FAQs.
Want to help us improve this content?